What is and ACL ?
- Ordered list of statements
- Permit/Deny
- A tool used not just for filtering but has many applications, including in route redistribution.
- Standard ACL only filters on source address
- Extended ACLs filters on source and destination

Not well-documented:
- Source ports are often not sho
15 permit tcp 123.0.0.0 0.255.255.255 gt 1023 4.0.0.0 0.255.255.255 eq telnet
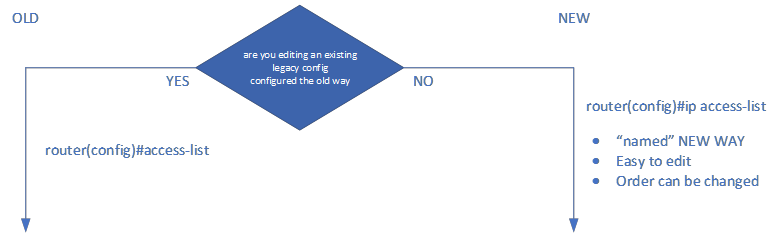
Numbered Access Lists:
Syntax: Numbered access lists are identified by a numeric ID (1 to 99 for standard ACLs, 100 to 199 for extended ACLs.
Inflexibility: With numbered ACLs, you cannot insert or delete entries without affecting the existing sequence. If you need to add or remove entries, you should renumber the ACL or reconfigure the entire list.
Named Access Lists:
Syntax: Named access lists are identified by a user-defined name. Names can be up to 64 characters long and are case-sensitive.
Flexibility: Named ACLs offer more flexibility because you can insert, delete, or modify entries without affecting the sequence of other entries.
Readability: Named ACLs are more human-readable than numbered ACLs because you can use descriptive names for the ACLs, making it easier to understand their purpose.
Scalability: Named ACLs support more ACL entries compared to numbered ACLs. They also support more extensive range options for ACL IDs (2000 to 2699).
Compatibility: Named ACLs are recommended for modern Cisco IOS versions, and they provide compatibility with IPv6 ACLs, which are only supported using named ACL syntax.
All ACLs / Firewall Filters
| Standard vs E | |
| Standard ACL example | permit 123.3.3.3 0.0.0.255 log |
| Extended ACL example | permit tcp 123.0.0.0 0.255.255.255 gt 1023 4.0.0.0 0.255.255.255 eq telnet |
| Numbered Access List | |
| Create the ACL | access-list 1 deny 123.3.3.3 0.0.0.0 log access-list 1 permit any |
interface ethernet 0/1 ip access-group 1 |
| Named Access list example | |
ip access-list extended DEMO | |
interface ethernet 0/1 | |
ip access-list |